Lab 15
Basic Network Troubleshooting Using MegaPing
MegaPing is an ultimate toolkit thatprovides complete essential utilities for information system administrator and IT solution providers.
Lab Scenario
You have learned in the previous lab that HTTP tunneling is a technique where communications within network protocols are captured using the HTTP protocol. For any companies to exist on the Internet, they require a web server. These web servers prove to be a high data value target for attackers. Tlie attacker usually exploits die WWW server running IIS and gains command line access to the system. Once a connection has been established, the attacker uploads a precompiled version o f the HTTP tunnel server (lits). With the lits server set up the attacker then starts a client on his 01־ her system and directs its traffic to the SRC port of the system running the lits server. This lits process listens on port 80 of the host WWW and redirects traffic. Tlie lits process captures the traffic in HTTP headers and forwards it to the WWW server port 80, after which the attacker tries to log in to the system; once access is gained he or she sets up additional tools to further exploit the network. MegaPing security scanner checks your network for potential vulnerabilities that might be used to attack your network, and saves information in security reports. in this lab you will learn to use MegaPing to check for vulnerabilities and troubleshoot issues.
Lab Objectives
This lab gives an insight into pinging to a destination address list. It teaches how to:
■ Ping a destination address list
■ Traceroute
■ Perform NetBIOS scanning
Lab Environment
To cany out die lab, you need:
■ MegaPing is located at D:\CEH-Tools\CEHv8 Module 03 Scanning Networks\Scanning Tools\MegaPing
■ You can also download the latest version of Megaping from the link http: / / www.magnetosoft.com/
■ If you decide to download the la te st version, then screenshots shown in the lab might differ
■ Administrative privileges to run tools
■ TCP/IP settings correcdy configured and an accessible DNS server
■ This lab will work in the CEH lab environment, on Windows Server 2012, Windows 2008, and Windows 7
Lab Duration
Time: 10 Minutes
Overview of Ping
Tlie ping command sends Internet Control Message Protocol (ICMP) echo request packets to die target host and waits for an ICMP response. During diis requestresponse process, ping measures die time from transmission to reception, known as die round-trip time, and records any loss packets.
Lab Tasks
1. Launch the Start menu by hovering die mouse cursor on the lower-left corner of the desktop.
 |
| FIGURE 13.1: Windows Server 2012 - Desktop view |
 |
| FIGURE 15.2: Windows Server 2012 - Apps |
 |
| Figure 15.3: MegaPing main windows |
5. Select IP scanner, and type in the IP range in die From and To field; in this lab the IP range is from 10.0.0.1 to 10.0.0.254. Click Start
6. You can select the IP range depending on your network.
 |
| FIGURE 15.4: MegaPing IP Scanning |
 |
| FIGURE 15.5: MegaPing IP Scanning Report |
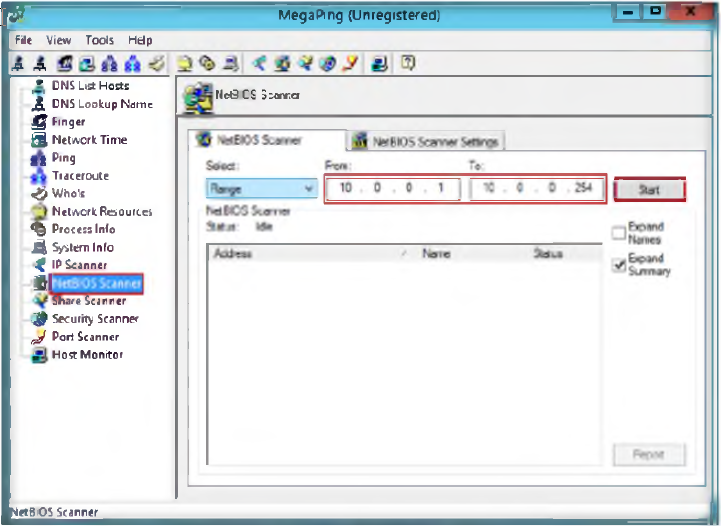 |
| FIGURE 15.6: MegaPing NetBIOS Scanning |
 |
| FIGURE 15.7: MegaPing NetBIOS Scanning Report |
11. Then, right-click and select the Traceroute option.
 |
| FIGURE 15.8: MegaPing Traceroute |
 |
| FIGURE 15.9: MegaPing Traceroute Report |
14. After clicking the Start button it toggles to Stop
15. It will lists the ports associated with www.certifiedl1acker.com with die keyword, risk, and port number.
 |
| FIGURE 15.10: MegaPing Port Scanning Report |
Document all die IP addresses, open ports and running applications, and protocols you discovered during die lab
Questions
1. How does MegaPing detect security vulnerabilities on die network?
2. Examine the report generation of MegaPing.


Không có nhận xét nào:
Đăng nhận xét